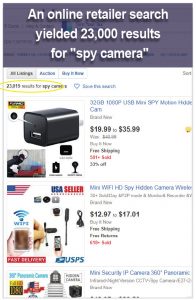
Protecting meeting spaces from illicit eavesdropping is a growing necessity. Start by ensuring there are no devices located inside the room itself, whether hidden or visible, that could be compromised for illicit purposes. Some examples of devices are desk phones, mobile phones, or audio recorders hidden in furniture or everyday items. Another threat that must not be neglected is audio leakage from surrounding surfaces and adjacent offices. These are vulnerabilities for both those listening in on your meeting with illicit intent or the passive observer in an adjacent office. Continue reading “Protecting Conversations With Noise Masking”
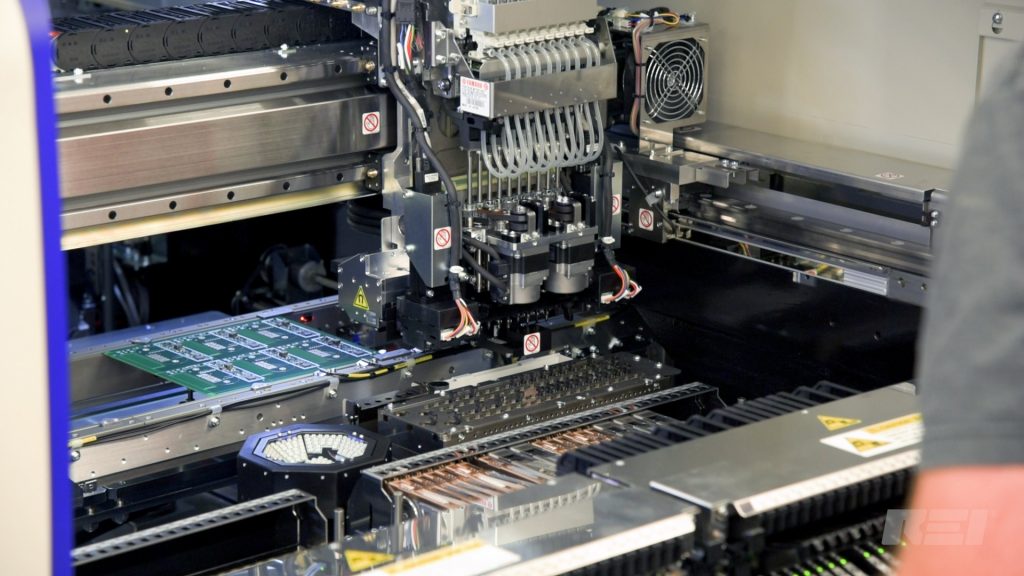 REI uses PnP (Pick and Place) machines to manufacture the circuit boards used in REI products. By upgrading these machines, REI is committed to providing the best technolgically advanced products possible in the near future.
REI uses PnP (Pick and Place) machines to manufacture the circuit boards used in REI products. By upgrading these machines, REI is committed to providing the best technolgically advanced products possible in the near future. 
 COOKEVILLE, TN – June, 2018 — Research Electronics International (REI), a leading manufacturer of counter-surveillance equipment, announces the release of the ANDRE Deluxe Near-Field Detection Receiver. The ANDRE detects signal activity and displays a histogram of signal strength over time. It is a handheld broadband receiver capable of detecting covert electronics including GSM bugs, microphones, cameras, RF and Wi-Fi transmitters, and mobile phones. Applications may include:
COOKEVILLE, TN – June, 2018 — Research Electronics International (REI), a leading manufacturer of counter-surveillance equipment, announces the release of the ANDRE Deluxe Near-Field Detection Receiver. The ANDRE detects signal activity and displays a histogram of signal strength over time. It is a handheld broadband receiver capable of detecting covert electronics including GSM bugs, microphones, cameras, RF and Wi-Fi transmitters, and mobile phones. Applications may include: