COOKEVILLE, TN, March 6, 2020 – Research Electronics International (REI) President, Tom Jones announced today the company will donate $20 thousand to the Cookeville-Putnam County Tornado Relief Fund, to help victims of the March 3rd tornado that hit middle Tennessee. Additionally, Victor H. Mendelson Co-President and Chief Executive Officer for HEICO Corporation’s Electronics Technology Group, REI’s parent company since June 2019, announced it will make a matching donation of $20 thousand for a combined contribution of $40 thousand.
COOKEVILLE, TN, March 6, 2020 – Research Electronics International (REI) President, Tom Jones announced today the company will donate $20 thousand to the Cookeville-Putnam County Tornado Relief Fund, to help victims of the March 3rd tornado that hit middle Tennessee. Additionally, Victor H. Mendelson Co-President and Chief Executive Officer for HEICO Corporation’s Electronics Technology Group, REI’s parent company since June 2019, announced it will make a matching donation of $20 thousand for a combined contribution of $40 thousand.
The fund was established to provide direct financial support to the victims of the tornado in the Cookeville-Putnam County area. The EF-4 tornado that caused 18 fatalities and tremendous damage throughout middle Tennessee, struck the area in the early morning hours, catching many people by surprise. “We have many friends and neighbors throughout this community who are really hurting from this tragedy, and we feel this is one of the ways we can help contribute to healing and rebuilding,” Jones said. “The people of middle Tennessee have shown tremendous character in the aftermath of this disaster with the turnout for relief efforts, and we know they are just beginning.”



 MIAMI & COOKEVILLE, Tenn.–(
MIAMI & COOKEVILLE, Tenn.–( The most commonly used antenna included with the ANDRE Near-field Detection Receiver is the Whip antenna. It is significantly larger than the other antennas and is an effective general-use antenna for locating RF signals. In this article, we will dig into how the whip antenna is designed and why it is considered the more commonly used antenna in the kit.
The most commonly used antenna included with the ANDRE Near-field Detection Receiver is the Whip antenna. It is significantly larger than the other antennas and is an effective general-use antenna for locating RF signals. In this article, we will dig into how the whip antenna is designed and why it is considered the more commonly used antenna in the kit.

 The Stage
The Stage
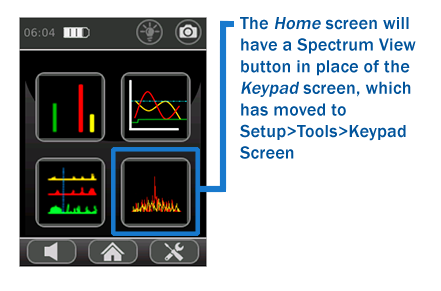 The ORION Non-Linear Junction Detector has a new firmware release for
The ORION Non-Linear Junction Detector has a new firmware release for